Suppose, you
have a personal computer and you use it every day just like everyone else does.
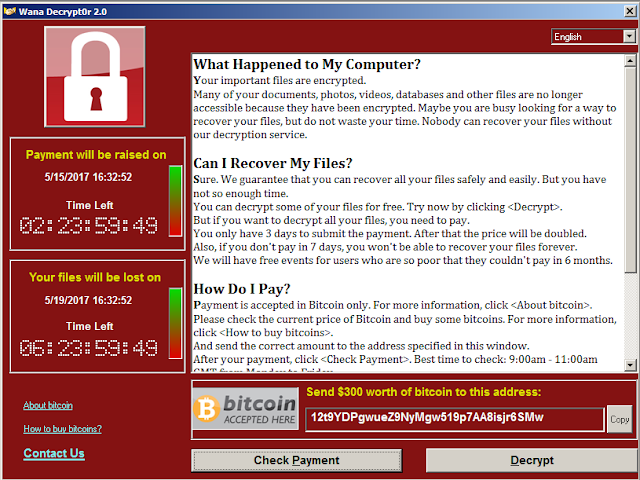
Now, one day you wake up, log on to your computer and see something really
unexpected, like this one:
Image Source: Panda Security
A ransomware!!
It has locked you out of your
computer, encrypted all your files with a magical wand and demanding a healthy
amount of money from you; Just to let you use your very own computer!!
What will
you do then? And even if you are not infected with this little hack tool, how
will you avoid the infection?
These are
the two topics we are going to discuss today.
At first, I
have to say, it’s a pretty scary name for a malware. Yes! It’s just a malware.
But a little more advanced one.
This idea of
extortion on computers gave birth to one of its first child in Russia, Belarus,
Ukraine, and Kazakhstan in 2005. Its name was TROJ_CRYZIP.A. Once downloaded and executed (by mistake of course!) it used
to locate files of certain types. Then it moved them to a password protected
zip file and showed the user this notification:
The users were
then asked to pay 300 USD to an E-Gold account owned by the hacker.
But the days
have changed. Hackers of today are more advanced and highly skilled. An E-Gold
account could easily for an attacker being tracked down and getting arrested.
Thus the
periodic evolution and development of the ransomwares made them stronger and leak
proof, resulting in WannaCry,
an advanced malware that uses bitcoin for fund transfer.
[Bitcoin is
an open source peer-to-peer money system. For more information, please visit
the following link:
WannaCry,
also known as WanaCrypt0r, WCry - spreads through your network connection. It
can also come as an email attachment, or as a file download from any
non-trusted site.
In 2014, the
attackers were able to wipe almost a terabyte’s worth of data from Sony
Picture’s database using this tool. The security system of the central bank of Bangladesh was breached by
a backdoor created by the makers of WannaCry in 2016, resulting in an $81m snatch.
Source:
If you are
infected with a ransomware, it’s advised not to pay any ransom. There is no surety
that the attackers will keep their word and decrypt your files. Moreover,
paying the attackers will be like contributing in the development of the
newer versions of this malware, which you surely don't want to do.
Instead, try
to decrypt the files by yourself. The popular antivirus companies are providing
effective and free tools to decrypt ransomware encrypted files.
- Avast is giving a wide range of decryption tools to decrypt your hacked data. The avast free antivirus also comes with a ransomware decryption tool.
- Kaspersky, AVG and Emsisoft are also providing a good set of decryptors.
- The Trendmicro and the Quickheal decryptor tools are also options worth checking.
Just visit
the links above, match your ransomware name and download the appropriate tool. Apply
it on the infected computer as directed. Hopefully you will be able to get your
files back. If so, then...
If you can’t do it by yourself, please contact with an expert to help you out.
And if your computer is not infected yet, please take necessary precautions.
- Don’t open unverified email attachments.
- Don’t visit malicious links.
- Don’t download and run any programs that you are not familiar with.
- Do update your computer on a regular basis.
- Do install a good antivirus or internet security.
- And spread the word, “You don’t have to pay any ransom!”
Microsoft
has released a security patch regarding WannaCry prevention. Please install it
from this
link.
One final
word, ransomware is not the only threat to your computer. Whether you are an
individual computer user or an entrepreneur or a business owner, your office
needs online security against hundreds of threats occurring every day.
Please
always try to avoid any kind of cyber-attack. Don’t react, be proactive. As
they say, prevention is better than cure.








No comments:
Post a Comment